Table of Contents
Overview
The YARA Analyzer module uses a set of rules to search files for textual or binary patterns. YARA was designed for malware analysis but can be used to search for any type of files. For more information on YARA see https://virustotal.github.io/yara/.
Configuration
To create and edit your rule sets, go to "Tools", "Options" and then select the "YARA" tab.
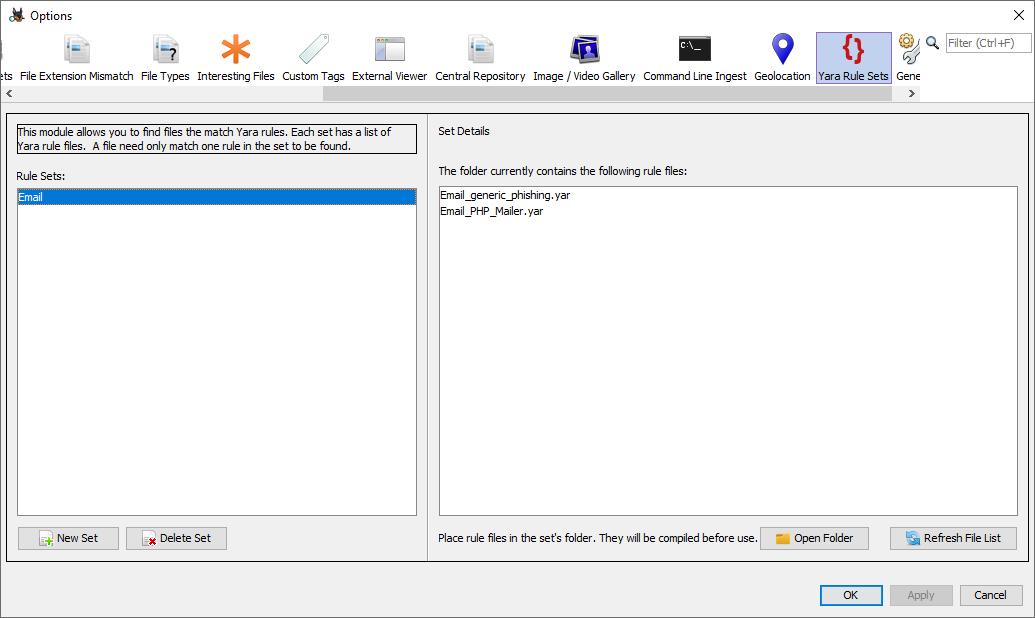
YARA rule sets are stored in folders in the user's Autopsy folder. To create a new rule set, click the "New Set" button in the lower left and enter the name for your new set.
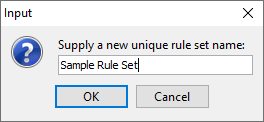
With your new rule set selected, click the "Open Folder" button to go to the newly created rules folder. You can now copy existing YARA files into this folder to include them in the rule set. Information on writing YARA rules can be found here and many existing YARA rules can be found through a web search. As a very simple example, we will add this rule to the sample rule set to find files that contain the words "hello" and "world":
rule HelloWorldRule
{
strings:
$part1 = "hello" nocase
$part2 = "world" nocase
condition:
$part1 and $part2
}
Once you've added your rules to the folder, click the "Refresh File List" button to show them in the options panel.
Running the Module
To enable the YARA Analyzer ingest module select the checkbox in the Ingest Modules configuration screen.
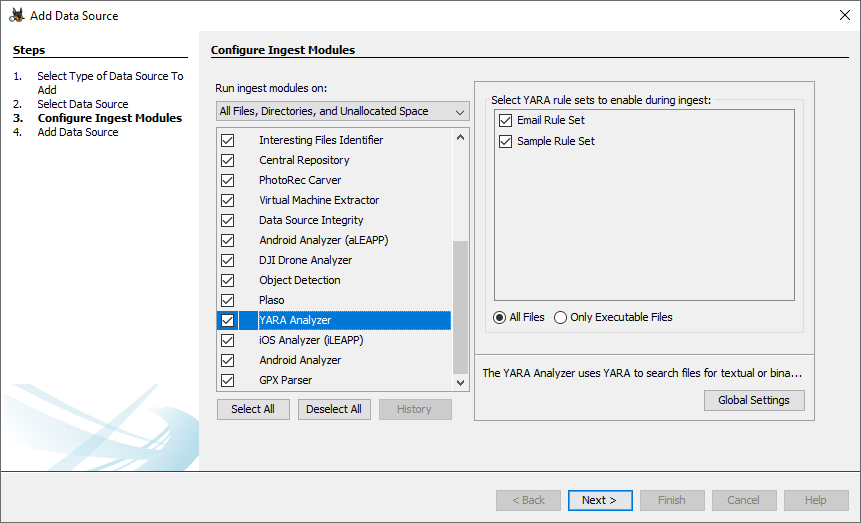
Make sure all rule sets you want to run are checked. You can also choose between running on all files or only running on executable files.
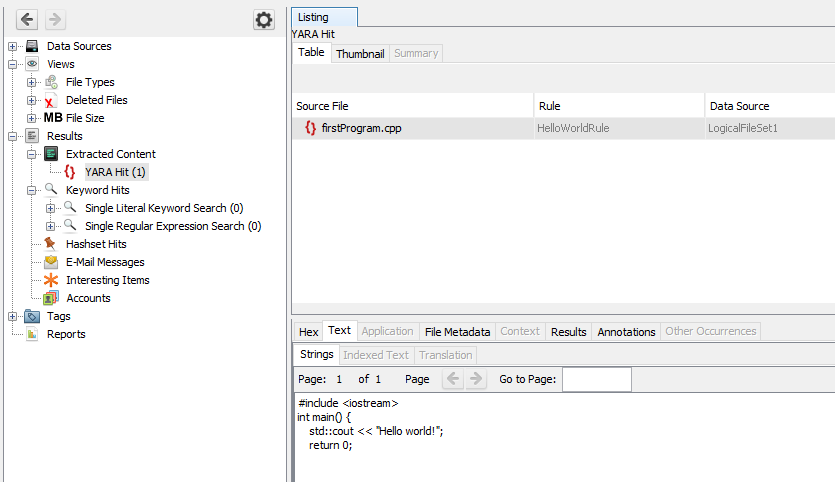
Viewing Results
Results are show in the Results tree under "Extracted Content".